JanelaRAT, a Remote Access Trojan (RAT), functions as a sophisticated piece of malicious software intended to grant remote access and control over compromised machines.
Observers have noted the utilization of JanelaRAT in attacks aimed at Latin American banking and financial institutions. The presence of Portuguese in the malware’s code strongly suggests that its developers are proficient in this language.
An Overview of the JanelaRAT Malware
JanelaRAT infiltrates systems via a multi-stage infection chain. This remote access trojan employs techniques to evade detection and analysis, incorporating heavily obfuscated code.
As previously stated, RATs establish remote access/control over infected devices. JanelaRAT is capable of executing shell commands. Its operations commence with the collection of pertinent machine data, such as device name, OS version, active user account, account type (admin, user, etc.), geolocation, etc.
Deployed in targeted attacks, JanelaRAT further hones its actions by monitoring active window titles to identify instances when data of interest is accessed, particularly financial and banking information. When the victim engages with targeted content, JanelaRAT initiates surveillance by capturing screenshots, recording keystrokes (keylogging), and tracing mouse movements and clicks.
This trojan can also replicate mouse movements and execute basic keyboard input (e.g., tab, arrow keys, etc.) within open programs. Additionally, JanelaRAT can display fabricated error messages, false screens indicating a Windows update in progress, and other deceptive imagery.
It’s important to note that malware developers frequently enhance their software and approaches. Consequently, potential future iterations of JanelaRAT could introduce different or additional functionalities and features.
| Name | JanelaRAT |
| Detection | Trojan:Win32/Wacatac.B!ml |
| Symptoms | Unauthorized monitoring of user activities through capturing screenshots, recording keystrokes, and tracking mouse movements and clicks. |
| Damage | JanelaRAT inflicts substantial damage by enabling unauthorized access to compromised systems, facilitating the theft of sensitive information, and exposing victims to potential financial loss and identity theft. |
| Fix Tool | See If Your System Has Been Affected by JanelaRAT Virus |
To summarize, the presence of malware like JanelaRAT on devices can lead to system infections, severe privacy breaches, financial repercussions, and identity theft.
Examples of Remote Access Trojans
We have extensively studied various malware samples, including RATs like XWorm, SeroXen, DarkVision, GhostRAT, Gh0stBins and Wise Remote Stealer, to name a few.
Remote access trojans exhibit remarkable versatility and encompass a wide array of capabilities. Moreover, some of these programs can trigger chain infections, such as downloading/installing ransomware, trojans, cryptocurrency miners, and the like.
Regardless of their operational methods, the existence of malware on a system jeopardizes both device and user security. Consequently, all threats should be promptly eradicated upon detection.
How JanelaRAT Infiltrated My Computer
JanelaRAT has been observed proliferating through ZIP archives containing VBScript, which initiates the subsequent stages of the malware’s infection process. However, the precise distribution mechanisms of these ZIP files remain unknown.
In most instances, cybercriminals disseminate malware using phishing and social engineering tactics. Malicious programs are often disguised as or bundled with ordinary software/media files, such as archives (ZIP, RAR, etc.), executables (.exe, .run, etc.), documents (Microsoft Office, Microsoft OneNote, PDF, etc.), JavaScript, and more.
Common distribution techniques include stealthy/deceptive drive-by downloads, malicious attachments and links in spam communications (emails, PMs/DMs, SMSes, etc.), online scams, malvertising, dubious download sources (freeware and third-party websites, Peer-to-Peer sharing networks, etc.), illegal program activation (“cracking”) tools, and counterfeit updates.
Furthermore, certain programs can self-propagate through local networks and removable storage devices (external hard drives, USB flash drives, etc.).
Preventing Malware Installation
We strongly advise exercising caution while browsing, as fraudulent and malicious online content often appears legitimate and harmless. Vigilance should extend to incoming emails and other messages. We recommend refraining from opening attachments and links from suspicious or irrelevant sources, as they might contain harmful elements.
Another precaution is to exclusively download from official and verified channels. Additionally, software should only be activated and updated using functions/tools provided by legitimate developers, as unauthorized activation tools (“cracks”) and third-party updaters could harbor malware.
We emphasize the critical nature of having a reliable and up-to-date antivirus solution. Security programs should be employed for regular system scans, detecting and eliminating identified threats and issues. If you suspect your computer is compromised, we suggest running an automatic scan with Gridinsoft Anti-Malware to eradicate infiltrated malware.
Remove JanelaRAT with Gridinsoft Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common Stealers as shown from our tests with the software, and we assure you that it can remove JanelaRAT as well as other malware hiding on your computer.
To use Gridinsoft for remove malicious threats, follow the steps below:
1. Begin by downloading Gridinsoft Anti-Malware, accessible via the blue button below or directly from the official website gridinsoft.com.
2.Once the Gridinsoft setup file (setup-gridinsoft-fix.exe) is downloaded, execute it by clicking on the file.
3.Follow the installation setup wizard's instructions diligently.
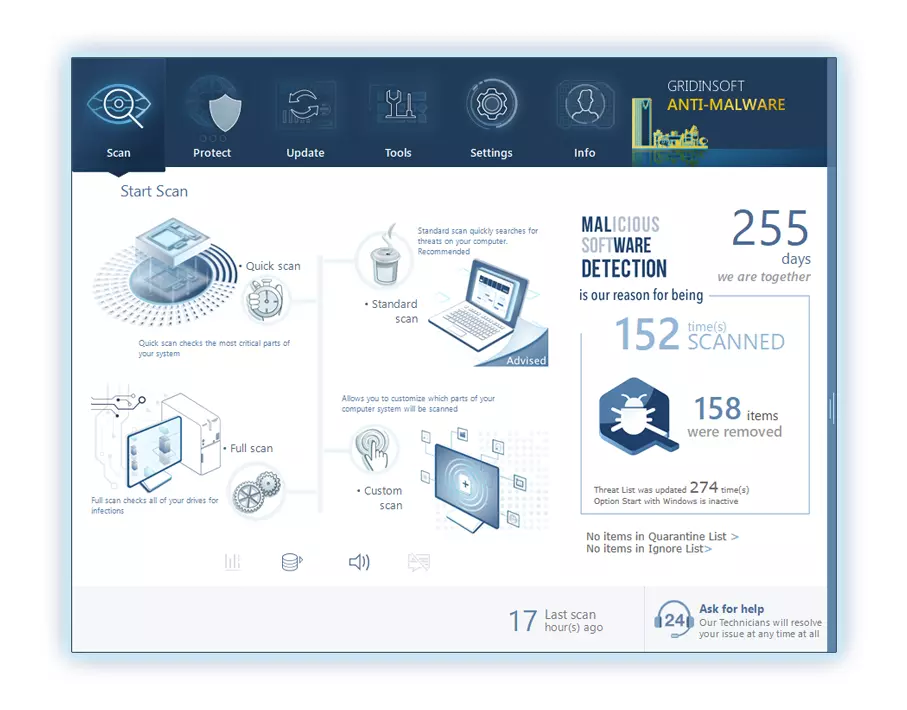
4. Access the "Scan Tab" on the application's start screen and launch a comprehensive "Full Scan" to examine your entire computer. This inclusive scan encompasses the memory, startup items, the registry, services, drivers, and all files, ensuring that it detects malware hidden in all possible locations.
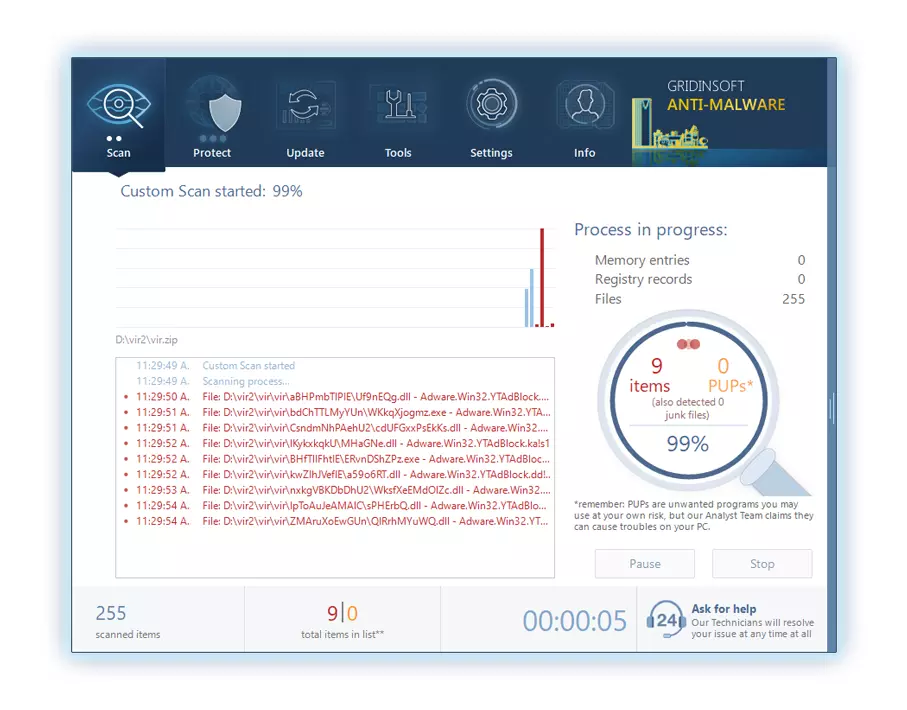
Be patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Use this time to relax or attend to other tasks.
5. Upon completion, Anti-Malware will present a detailed report containing all the detected malicious items and threats on your PC.
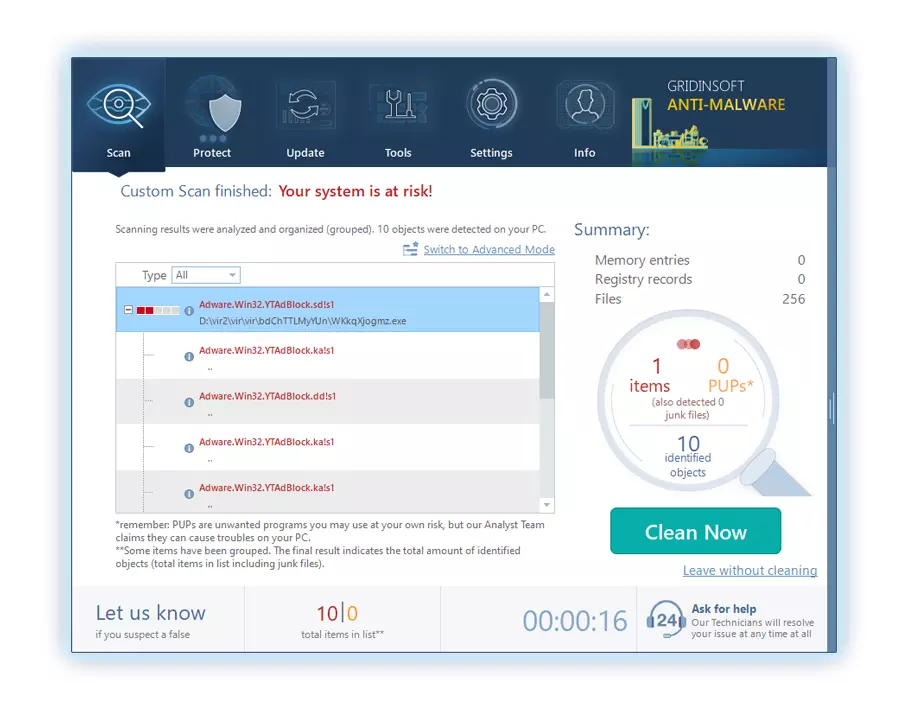
6. Select all the identified items from the report and confidently click the "Clean Now" button. This action will safely remove the malicious files from your computer, transferring them to the secure quarantine zone of the anti-malware program to prevent any further harmful actions.
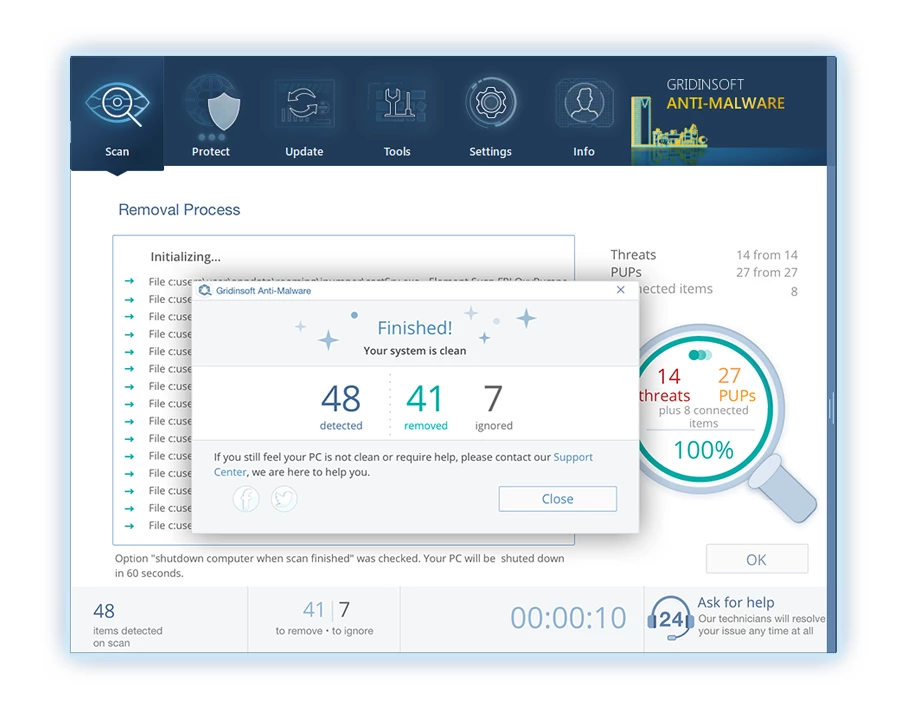
8. If prompted, restart your computer to finalize the full system scan procedure. This step is crucial to ensure thorough removal of any remaining threats. After the restart, Gridinsoft Anti-Malware will open and display a message confirming the completion of the scan.
Remember Gridinsoft offers a 6-day free trial. This means you can take advantage of the trial period at no cost to experience the full benefits of the software and prevent any future malware infections on your system. Embrace this opportunity to fortify your computer's security without any financial commitment.
Trojan Killer for “JanelaRAT” removal on locked PC
In situations where it becomes impossible to download antivirus applications directly onto the infected computer due to malware blocking access to websites, an alternative solution is to utilize the Trojan Killer application.
There is a really little number of security tools that are able to be set up on the USB drives, and antiviruses that can do so in most cases require to obtain quite an expensive license. For this instance, I can recommend you to use another solution of GridinSoft - Trojan Killer Portable. It has a 14-days cost-free trial mode that offers the entire features of the paid version. This term will definitely be 100% enough to wipe malware out.
Trojan Killer is a valuable tool in your cybersecurity arsenal, helping you to effectively remove malware from infected computers. Now, we will walk you through the process of using Trojan Killer from a USB flash drive to scan and remove malware on an infected PC. Remember, always obtain permission to scan and remove malware from a computer that you do not own.
Step 1: Download & Install Trojan Killer on a Clean Computer:
1. Go to the official GridinSoft website (gridinsoft.com) and download Trojan Killer to a computer that is not infected.
2. Insert a USB flash drive into this computer.
3. Install Trojan Killer to the "removable drive" following the on-screen instructions.
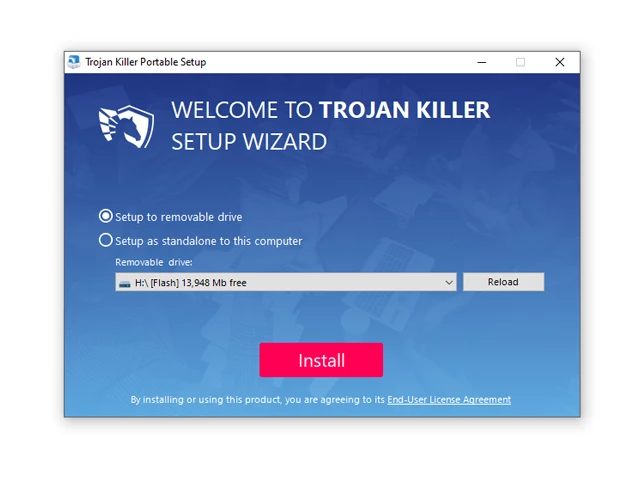
4. Once the installation is complete, launch Trojan Killer.
Step 2: Update Signature Databases:
5. After launching Trojan Killer, ensure that your computer is connected to the Internet.
6. Click "Update" icon to download the latest signature databases, which will ensure the tool can detect the most recent threats.
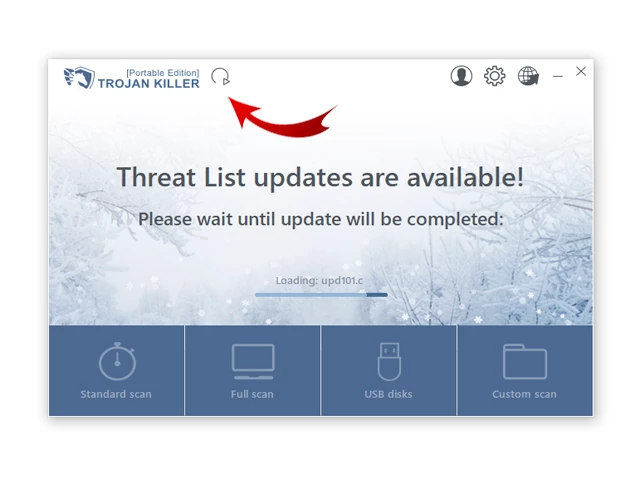
Step 3: Scan the Infected PC:
7. Safely eject the USB flash drive from the clean computer.
8. Boot the infected computer to the Safe Mode.
9. Insert the USB flash drive.
10. Run tk.exe
11. Once the program is open, click on "Full Scan" to begin the malware scanning process.
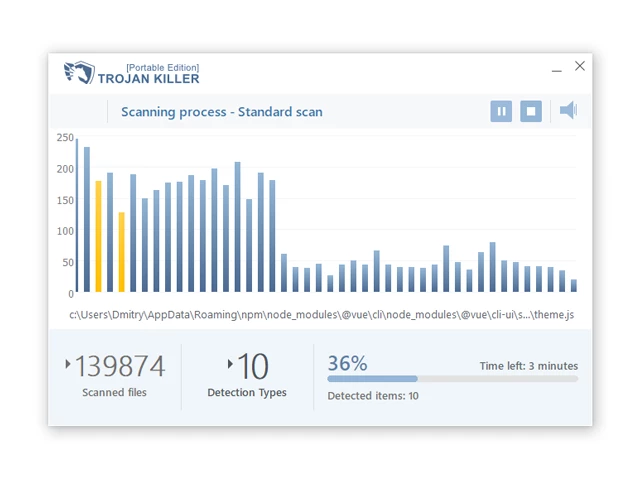
Step 4: Remove Found Threats:
12. After the scan is complete, Trojan Killer will display a list of detected threats.
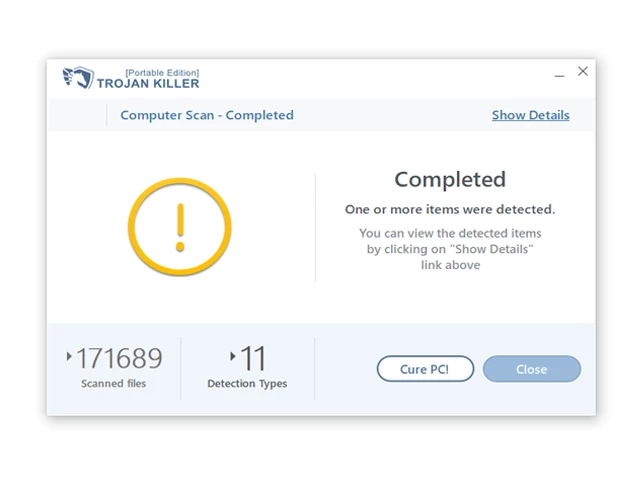
13. Click on "Cure PC!" to remove the identified malware from the infected PC.
14. Follow any additional on-screen prompts to complete the removal process.
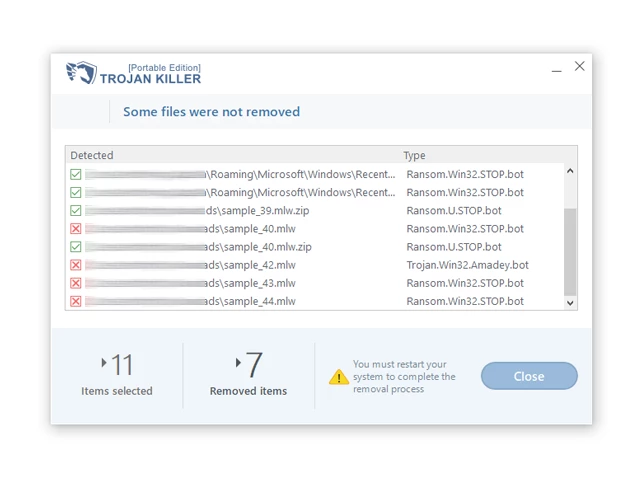
Step 5: Restart Your Computer:
15. Once the threats are removed, click on "Restart PC" to reboot your computer.
16. Remove the USB flash drive from the infected computer.
Congratulations on effectively removing JanelaRAT and the concealed threats from your computer! You can now have peace of mind, knowing that they won't resurface again. Thanks to Gridinsoft's capabilities and commitment to cybersecurity, your system is now protected.
Frequently Asked Questions (FAQ)
JanelaRAT is a Remote Access Trojan (RAT) that functions as a sophisticated piece of malicious software aimed at providing remote access and control over compromised computer systems.
JanelaRAT is often spread through malicious attachments, links, or files embedded in phishing emails, websites, or other forms of social engineering. It has been observed to infiltrate systems via ZIP archives containing VBScript.
The main objective of JanelaRAT is to enable cybercriminals to gain unauthorized access to compromised machines, allowing them to monitor activities, steal sensitive data (such as financial and personal information), and potentially execute malicious commands.
JanelaRAT establishes remote access by employing multi-stage infection chains. It can execute shell commands, capture screenshots, record keystrokes (keylogging), and track mouse movements and clicks to monitor user activities.
JanelaRAT employs anti-detection and anti-analysis techniques to evade security measures. This includes incorporating heavily obfuscated code and monitoring active window titles to avoid detection while capturing sensitive data.
Prevention and detection strategies include maintaining up-to-date security software and antivirus solutions, being cautious with email attachments and links, downloading software only from official sources, and performing regular system scans.
JanelaRAT infections pose serious risks, including unauthorized access to personal and financial information, potential financial losses, identity theft, system instability, and the possibility of further malware installation.
JanelaRAT has been observed in attacks targeting Latin American banking and financial institutions, where its capabilities enable cybercriminals to access and potentially manipulate financial data, leading to monetary losses and potential reputational damage.
Yes, malware like JanelaRAT can evolve through updates and modifications introduced by its developers. This could result in the introduction of new functionalities, evasion techniques, and distribution methods.
Users should exercise caution when interacting with emails, avoid opening suspicious attachments or links, keep their operating systems and software up to date, use strong and unique passwords, and regularly back up their data to minimize potential damage from a JanelaRAT infection.
What is JanelaRAT?
Name: JanelaRAT
Description: JanelaRAT is a type of Remote Access Trojan (RAT), which is a malicious software designed to infiltrate and compromise computer systems, providing unauthorized remote access and control to cybercriminals.
Operating System: Windows
Application Category: Malware


